CryptoverseCTF 2023
Hi Mates!
I participated in the Cryptoverse CTF 2023, a 36-hour competition designed for beginner to intermediate players. The event focused on cryptography, reverse engineering, and programming. Our team managed to achieve 58th place in the competition.
Here are some of the challenges I have solved :
Crypto/Warmup 3 #
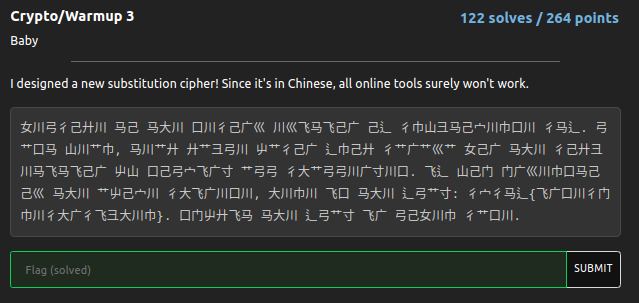
女川弓彳己廾川 马己 马大川 口川彳己广巛 川巛飞马飞己广 己辶 彳巾山彐马己宀川巾口川 彳马辶. 弓艹口马 山川艹巾, 马川艹廾 廾艹彐弓川 屮艹彳己广 辶巾己廾 彳艹广艹巛艹 女己广 马大川 彳己廾彐川马飞马飞己广 屮山 口己弓宀飞广寸 艹弓弓 彳大艹弓弓川广寸川口. 飞辶 山己门 门广巛川巾口马己己巛 马大川 艹屮己宀川 彳大飞广川口川, 大川巾川 飞口 马大川 辶弓艹寸: 彳宀彳马辶{飞广口川彳门巾川彳大广彳飞彐大川巾}. 口门屮廾飞马 马大川 辶弓艹寸 飞广 弓己女川巾 彳艹口川.
Based on the challenge description, it is clear that a new substitution cipher has been designed, and the text is written in Chinese. The challenge also mentions that “online tools won’t work” in solving the cipher.
Initially, the approach of translating the Chinese text to English and then using a substitution cipher decoder may seem like a viable solution. However, it turns out that my assumption was wrong🥲.
Although translating the text did not confirm my assumption, I am confident that I can randomly assign English alphabets to the Chinese characters based on their respective patterns. Initially, I tried to solve it manually with pen & paper for each character, but it was more time-consuming than I anticipated.
Therefore, I wrote a small Python script to automate the process🪄.
CODE :
import re
def replace_chars(s):
char_map = {
"女": "A",
"川": "B",
"弓": "C",
"彳": "D",
"己": "E",
"廾": "F",
"马": "G",
"口": "H",
"广": "I",
"巛": "J",
"巾": "K",
"山": "L",
"彐": "M",
"宀": "N",
"艹": "O",
"屮": "P",
"寸": "Q",
"门": "R",
"飞": "S",
"辶": "T",
"丷": "U",
"夕": "V",
"大": "W",
"弋": "X",
"乙": "Y",
"彡": "Z"
}
result = re.sub("[\u4e00-\u9fff]", lambda x: char_map[x.group()], s)
return result
s = "女川弓彳己廾川 马己 马大川 口川彳己广巛 川巛飞马飞己广 己辶 彳巾山彐马己宀川巾口川 彳马辶. 弓艹口马 山川艹巾, 马川艹廾 廾艹彐弓川 屮艹彳己广 辶巾己廾 彳艹广艹巛艹 女己广 马大川 彳己廾彐川马飞马飞己广 屮山 口己弓宀飞广寸 艹弓弓 彳大艹弓弓川广寸川口. 飞辶 山己门 门广巛川巾口马己己巛 马大川 艹屮己宀川 彳大飞广川口川, 大川巾川 飞口 马大川 辶弓艹寸: 彳宀彳马辶{飞广口川彳门巾川彳大广彳飞彐大川巾}. 口门屮廾飞马 马大川 辶弓艹寸 飞广 弓己女川巾 彳艹口川."
result = replace_chars(s)
print(result)
Here is the actual output:
m4r10@ARLinux:~/Desktop/CyberSec/CTF/cvCTF/crypto/warmup3$ python3 temp.py
ABCDEFB GE GWB HBDEIJ BJSGSEI ET DKLMGENBKHB DGT. COHG LBOK, GBOF FOMCB PODEI TKEF DOIOJO AEI GWB DEFMBGSGSEI PL HECNSIQ OCC DWOCCBIQBH. ST LER RIJBKHGEEJ GWB OPENB DWSIBHB, WBKB SH GWB TCOQ: DNDGT{SIHBDRKBDWIDSMWBK}. HRPFSG GWB TCOQ SI CEABK DOHB.
Then, I used a substitution cipher decoder called quipqiup.
Output :
WELCOME TO THE SECOND EDITION OF CRYPTOVERSE CTF. LAST YEAR, TEAM MAPLE BACON FROM CANADA WON THE COMPETITION BY SOLVING ALL CHALLENGES. IF YOU UNDERSTOOD THE ABOVE CHINESE, HERE IS THE FLAG: CVCTF{INSECURECHNCIPHER}. SUBMIT THE FLAG IN LOWER CASE.
Flag : cvctf{insecurechncipher}
Misc/Reset Options #
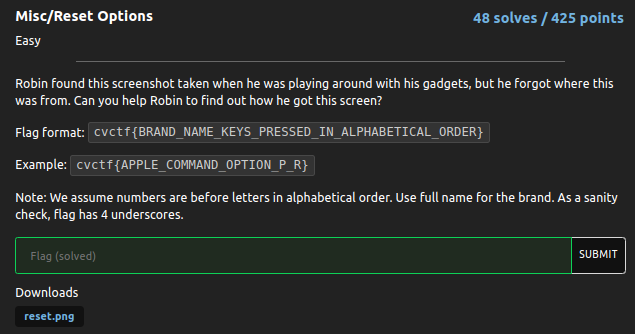
Robin found this screenshot taken when he was playing around with his gadgets, but he forgot where this was from. Can you help Robin to find out how he got this screen?
Flag format: cvctf{BRAND_NAME_KEYS_PRESSED_IN_ALPHABETICAL_ORDER}
Example: cvctf{APPLE_COMMAND_OPTION_P_R}
Note: We assume numbers are before letters in alphabetical order. Use full name for the brand. As a sanity check, flag has 4 underscores.
First, I examined the given PNG file, then used Google Lens to search for the brand name, and I found TI-84 (Calculator)
that is : TEXAS INSTRUMENTS
After, I got original PNG file with additional information from This
After observing the above image and reading the challenge note, I created a flag format
Flag : cvctf{TEXAS_INSTRUMENTS_8_2_ON}